Navigating the Procurement Cybersecurity Battleground: Safeguard Your Company
Every day, hackers are snatching data and throwing wrenches into business operations. With out proper procurement cybersecurity practices, your organization could be their next victim. In fact, cybercrime is an estimated $8 trillion problem that’s expected to swell to $10.5 trillion by 2025. ¹
Cybercriminals are getting smarter, too, finding sneaky ways to slip into your organization through your suppliers. Last year, ransomware attacks on suppliers accounted for 50% of all supply chain disruptions.²
But there’s hope.
Unmasking Cybercrime: More Than a Hoodie and a Keyboard

When you think of a hacker, do you picture a person in a stained t-shirt typing away on a keyboard in a dark room? Often, people don’t realize that this is an entire industry.
“It’s almost an industrial complex,” says David Coles, Threat Intelligence Director. “The person who sends the phishing email that steals your password is not the same person who steals your data. And that’s not even the same person who encrypts your computer and holds it for ransom. They’re all different people and stages in a multi-trillion dollar industry.”
And these cybercriminal groups are highly organized. They operate through “access shops” or underground online marketplaces where they buy and sell unauthorized access to compromised systems, networks, passwords, and user accounts.
“Hackers are real people, not machines or viruses,” says Charles Clark, CEO of Darkbeam. “They’re real people with the intent to make a lot of money from what they do.”
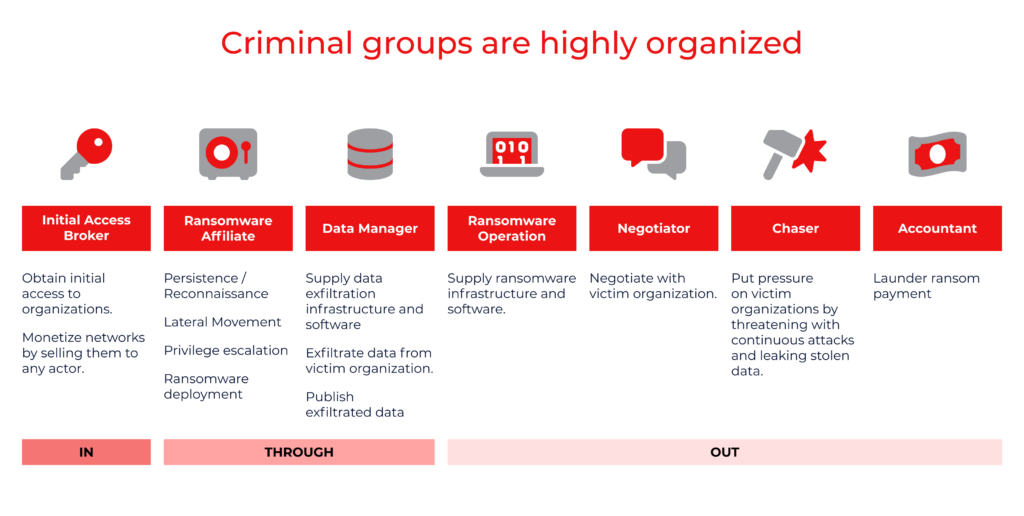
These underground cyber-marketplaces sell access to:
- Compromised accounts: Social media profiles, email, online banking accounts, and more.
- Corporate networks: Company networks where cybercriminals steal sensitive data, disrupt operations, or carry out further attacks.
- E-commerce platforms: Online stores where hackers perform fraudulent transactions or steal customer information.
- Healthcare systems: Patient records, medical databases, or hospital networks for data theft or ransomware attacks.
- Financial institutions: Banking systems, trading platforms, and other payment gateways.
- Government systems: Government databases, municipal networks, or sensitive government resources.
How Are Would-be Attackers Slipping In?
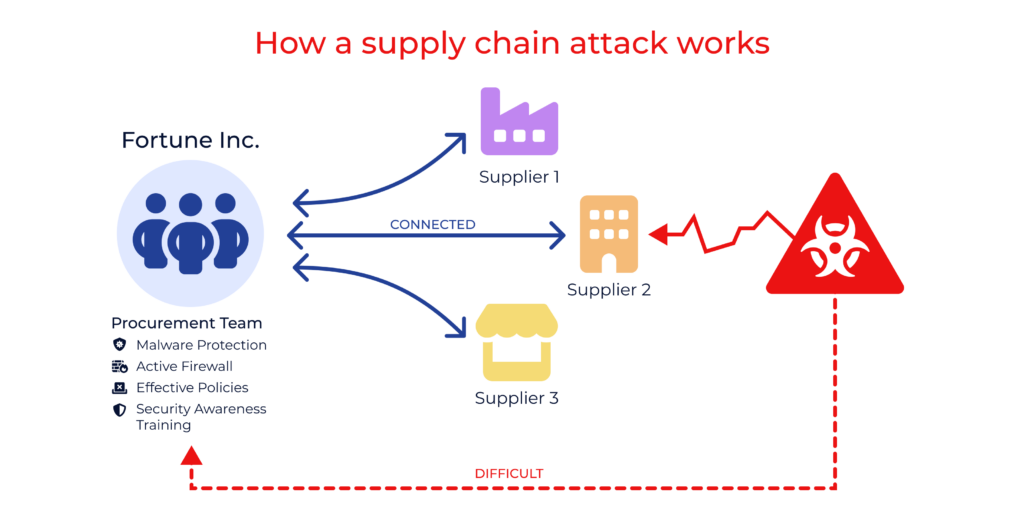
Hackers are clever and seek the easiest entry points. One way they breach an organization’s defenses is by piggybacking onto suppliers, similar to how Greek soldiers captured the besieged city of Troy by hiding in the Trojan horse.
“Over the past three to four years, [cybercriminals’] tactics have advanced significantly, and they’ve become deeply effective in their approach,” says Clark. “The prize is considerably bigger than going directly at a customer since one supply chain hack results in multiple opportunities to make money.”
Consider a large technology company that invests extensively in fortifying its “castle” walls with robust security measures. Instead of attempting a direct assault on their formidable defenses, hackers will target a potential weak link—the smaller suppliers they do business with.
Typically less fortified, these suppliers can serve as gateways to valuable assets. By infiltrating a supplier who interfaces with the tech company or has access to their data, hackers can gain entry to the “crown jewels”—sensitive information that holds significant value—and often from the most obscure areas.
Assessing the Value at Risk in Your Supply Chain
In today’s interconnected world, supply chain resilience is more critical than ever. The recent surge in cyberattacks and disruptions has highlighted the need for companies to identify and mitigate risks in their supply chains. How do you determine which suppliers pose the most significant risks to your organization? The key lies in assessing the “Value at Risk.”
What Is Value at Risk?
Value at Risk (VaR) is a metric that helps quantify the potential financial impact of a disruption or breach within your supply chain. It goes beyond the size of the supplier or the amount of money you spend with them. Even seemingly minor suppliers can have far-reaching consequences if they experience a breach.
For example, a small parts supplier for Toyota fell victim to a ransomware attack, resulting in a day-long system shutdown. This seemingly minor incident cost Toyota 13,000 cars, equivalent to 5% of its monthly production output. The value at risk here was significant, far beyond the immediate cost of components.
Understanding the Ripple Effect
Supply chain disruptions can trigger cascading effects, including service interruptions, product issues, and potential data exposure. It’s easy to underestimate the impact of a breach with a seemingly insignificant supplier. The true risk lies in the knock-on effects that can disrupt your operations or compromise sensitive data, says Clark.
For instance, a supplier breach exposed classified blueprints of SpaceX rocket components, posing a threat to national security. Even more recently, on September 11, 2023, MGM Resorts International was hit with a cyberattack that shut down operations at major casinos in Las Vegas and properties around the United States. In another case, a UK telecommunications firm lost over 100,000 customers and faced substantial costs due to a third-party cybersecurity incident, including hefty fines.
Calculating Risk: Probability and Impact
To assess supply chain risk effectively, consider both the probability of a breach occurring and the potential impact on your business. That means looking beyond the cost of the products or services to incorporate factors like reliability, quality, and the supplier’s overall impact on your operations.
Think of it as a probability and impact equation. When you know exactly how much you spend with each supplier, you can calculate these probabilities and impacts more accurately. It’s like having a clear roadmap to identify potential obstacles in your supply chain. Regardless of the size of a supplier, understanding both the likelihood and the potential consequences of a breach empowers you to make informed decisions and fortify your supply chain resilience.
Identify and Assess Cyber Threats in Your Supply Chain
Consider the following strategies and tools to help you proactively detect and evaluate cyber threats within your supply chain:
Supplier risk assessment: Conduct a thorough risk assessment before onboarding a new supplier. Clark recommends asking if the supplier is connected to your network or has access to your data. In addition, examine their cybersecurity practices, protocols, and past incident history. Use questionnaires, audits, and site visits to evaluate their security posture.
Continuous monitoring: Monitor your suppliers’ cybersecurity activities and practices closely. Set up automated alerts to receive real-time notifications about emerging threats that could impact your suppliers.
Threat intelligence: Leverage external threat sources to gather information about cyber threats targeting your industry or region. Subscribing to threat feeds can provide up-to-the-minute insights into potential risks.
Cybersecurity frameworks: Implement recognized cybersecurity frameworks such as NIST or ISO 27001 for your suppliers to follow as they offer guidelines for robust cybersecurity practices.
Third-party risk management platforms: Invest in third-party risk management (TPRM) platforms. For instance, Darkbeam and Graphite work in tandem to streamline the assessment of your suppliers’ cybersecurity posture.
Supply chain analytics: Use analytics tools to monitor your supply chain’s data flows and communication patterns. Detect anomalies or suspicious activities that may indicate a cyber threat.
Red teaming and vulnerability assessments: Simulate real-world attacks through red teaming exercises to identify vulnerabilities. Collaborate with suppliers on joint vulnerability assessments to pinpoint weaknesses in systems and processes.
Contractual agreements: Include cybersecurity clauses in your supplier contracts, specifying security requirements and incident reporting obligations. Legally bind suppliers to maintain a certain level of cybersecurity.
Incident response planning: Collaborate with suppliers to develop joint incident response plans. Clearly outline how both parties will cooperate and coordinate in case of a cyber incident.
Training and awareness: Provide cybersecurity training to suppliers’ personnel to ensure they understand and follow security best practices.
By combining these strategies and tools, your organization can proactively identify threats within your supply chain and minimize the risk of disruptive cyber incidents that could compromise sensitive data and tarnish your reputation.
Shine a Light on Potential Vulnerabilities & Threats

“Hackers have already won the game in this multi-trillion-dollar industry. Our mission is clear: to reduce risk and safeguard our digital fortresses,” says Clark.
Gaining deeper visibility into your supply chain is the key to proactively identifying and evaluating cyber threats–and avoiding potential security breaches. Yet, 69% of companies do not have complete visibility over their supply chains.³
“Too often, a supplier doesn’t even know they’ve been breached. This is where the collaboration between Darkbeam and Graphite truly shines in the ever-evolving cybersecurity landscape,” says Smith. “Our partnership equips organizations with unparalleled insights into their supply chains, illuminating potential vulnerabilities and access points. You can see what data your suppliers can access, their connections to your network, and how close they are to your ‘crown jewels.’ This enhanced visibility empowers us to proactively detect and stop an incident before it becomes serious.”
In an era where cyber threats are increasingly pervasive and sophisticated, swift and proactive responses are paramount. The Darkbeam and Graphite partnership offers businesses the means to stay ahead of cybercriminals by detecting digital weaknesses, identifying at-risk suppliers, and responding promptly to mitigate the impact of potential cyberattacks.
At Graphite Connect, we provide the tools and partnerships to help procurement teams work smarter and faster. Our proven supplier lifecycle and risk management tool can help you proactively identify threats and minimize the risk of disruptive and costly cyber events.
Contact us to learn how you can better protect your assets and stay cyber-resilient.
Ready to Learn More?
When you’re ready to better understand the cyber risk exposure of your supply chain, let’s chat.
Request a DemoReferences:
¹ “Cybercrime to Cost the World 8 Trillion Annually in 2023,” Cybercrime Magazine, October 17, 2022.
https://cybersecurityventures.com/cybercrime-to-cost-the-world-8-trillion-annually-in-2023/
² Business Continuity Institute. www.thebci.org
³ “97 Supply Chain Statistics You Must Know: 2023 Market Share Analysis & Data,” FinancesOnline. https://financesonline.com/supply-chain-statistics
