Conquer Supplier Risk Using the TAME Framework
Once you’ve identified and rated your supplier risk based on potential impact and likelihood, the next step is developing management strategies for each supplier. There are four risk management options under the TAME framework: Transfer, Accept, Mitigate, and Eliminate.
Transfer Risk
Transferring the risk involves offloading the financial consequences of the risk to a third party, such as an insurance company. For example, when investing in a policy, the insurance company assumes all financial liabilities associated with the risk domain (legal expenses, damages awarded, and repair costs).
Accept Risk
Accepting risk means that your organization recognizes the potential consequences of the risk but decides to continue with the activity regardless. If this method is chosen, remember to evaluate the risk regularly and escalate if necessary. Finally, even if you select the “do nothing” strategy, the risk domain must still have an assigned risk owner who can be held accountable if things go awry.
Mitigate Residual Risk
Mitigating the risk involves reducing the probability and impact of the risk. It is essential to pick a framework for each risk factor. Frameworks provide a structured approach to risk management and ensure that all relevant factors are considered. There are many frameworks available depending on the specific risk factor.
Traditional cybersecurity frameworks include the National Institute of Standards and Technology (NIST), which provides a comprehensive cybersecurity framework for organizations, and the Low-Moderate-Advanced (LMA) framework, which helps organizations prioritize cybersecurity efforts based on their risk profiles.
Another one is the American Institute of Certified Public Accountants (AICPA) framework, which provides a structured approach to identifying and managing cybersecurity risks.
For privacy-related risks, some frameworks include the Service Organization Control 2 (SOC 2), which helps organizations manage risks related to protecting customer data, and the General Data Protection Regulation (GDPR), which provides a framework for managing risks associated with collecting, storing, and processing personal data.
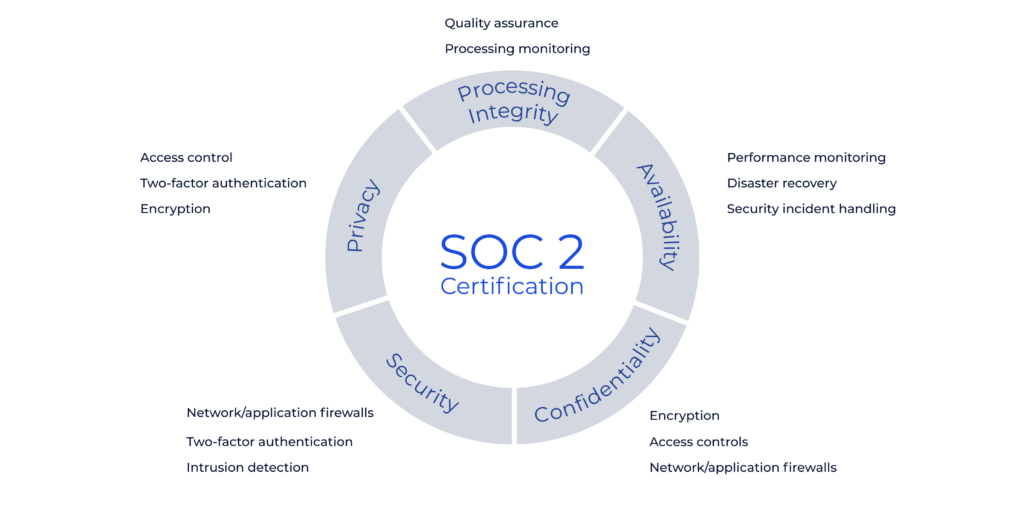
Implementing risk policies based on these frameworks is critical to managing risks effectively. It helps ensure that all relevant factors are considered and that the organization addresses the most significant risks.
Furthermore, a structured approach helps ensure your organization complies with applicable laws and regulations and reduces the risk of reputational damage.
Eliminate Inherent Risk
Eliminating the risk is the most radical approach and typically involves abstaining from activities that could expose the organization to a particular risk. Elimination is only possible for risks like too-broad system access across your organization. Furthermore, risk elimination is generally the most costly strategy.
Once you’ve developed effective strategies to manage your identified risks, you’ll want to monitor them regularly.
Want to know more?
Read our e-book to learn how to build a solid risk management process that protects your organization against potential threats.
Read the Ebook