Get Started
Graphite's supplier management tool helps you onboard faster, cut time on risk reviews and streamline supplier validations. Save time and money.
April 12 2023
Combining Procurement and Security to Mitigate Risk
How are new tools and applications introduced into your organization? Is there a link between procurement and security? If employees purchase technology without going through the proper security and IT channels, it could expose your business to some serious (not to mention expensive!) compliance and regulatory issues.
In this e-book, learn how to partner with your IT and security teams to mitigate risk and drive business value.
Today’s agile workplace requires employees to work more efficiently than ever before. As a result, they’re constantly adopting new tools and applications to help them. But if your IT department doesn’t authorize this new technology, it can bring additional risks into your supply chain.
“People have this on-demand attitude of ‘I needed this yesterday,’” says Aaron Oyler, Chief Product Officer for Graphite Connect. “If the company culture is about getting things out the door as quickly as possible, you will always default to the business and getting things done as fast as you can, but not necessarily doing them appropriately.”
Poor Procurement Security Leads to Shadow IT
Implementing technology that bypasses the proper security channels—called shadow IT—is common in businesses. A recent Forbes article cites Gartner reporting that 30 to 40% of tech spending in large enterprises goes to shadow IT, while the Everest Group found shadow IT spending even higher—at 50%.¹
The problem with this spontaneous approach to onboarding tech is that it exposes your organization to costly and time-consuming security and compliance concerns that could damage your reputation and your bottom line. Essentially, it removes security from the procurement process.
“Sure, you’ll have the breeze of flipping the credit card and getting a tool, but six to nine months from now, it’s not going to do what you want,” says Robert Haldeman, CEO/CSO at CYBER1GRC. “You paid for something you can’t afford to fix, and now it’s problematically compounded.”
Incorporating IT Security into the Procurement Process
Procurement is the gate between a business unit defining a need and sourcing a product or tool to fulfill that need. Procurement security is critical but it can only be guaranteed by getting IT involved from the beginning.
An immature organization may have a history of getting to the contract phase and buying products or services before anyone in IT has reviewed the architectural and design specifications. On the other hand, a mature company recognizes the importance of designing security into the procurement process to ensure visibility and accountability throughout the entire lifecycle.
“People think of security as icing. They build the cake and then realize, ‘Oh yeah, we need that security icing.’ So they put that icing on at the end, and then the threat actor comes along, scrapes off the icing, and there’s the whole cake for them.” says Scott Schindler, CISO for Logos Systems. “You cannot do that. Security has to be one of the main ingredients of the cake. Not just the icing.”
When you engage security and IT as an integral part of your procurement process, you help to ensure the products and services you acquire meet your company’s security and technical requirements—and save some major headaches in the future. Here are some guidelines to help you:
Ensure Procurement Information Security by Involving IT from the Start
Get security and IT involved right out of the gate to provide input on technical requirements and help you choose the suppliers and products that best meet those requirements. This will not only help you address any issues that arise promptly but also take care of procurement information security.
“If you want to do it right, you have to engage up front in the contracting and procurement process and get security built into the cake, like the eggs or the flour, as part of the cake, not just something thrown on after baking it,” says Oyler.
For best results, you need a Chief Information Security Officer (CISO) or a head of IT that is driving the security piece in your procurement process. This person is accountable for meeting regulatory and security requirements.
“Without a qualified security leader driving security by design into this process, it’s irrelevant what companies do,” says Schindler. “They’re always going to do it wrong, they’re going to do it cheaply, and they’re going to do it haphazardly, and, as a result, open themselves up to unnecessary risk.”
Create Rounded Policies for Security in the Procurement Process
Develop procedures that specify the roles and responsibilities of the security and IT teams within the procurement process. In addition, include guidelines around assessing your third-party suppliers’ security and technical capabilities.
“Procurement holds the purse strings,” Oyler says. “And the best way to get the business to do something is to say you’ll hold up the money until these steps are followed. We won’t sign the contract until you’ve checked all the boxes.”
Develop a workflow for onboarding new technology
Build a procurement workflow unique to your organization’s business needs. Include all the pieces that require reviews, such as the technology, architecture, project plan, and third-party management.
The workflow below shows how procurement and security teams can effectively work together when onboarding new technology.
Here are the basic steps in the onboarding technology process:
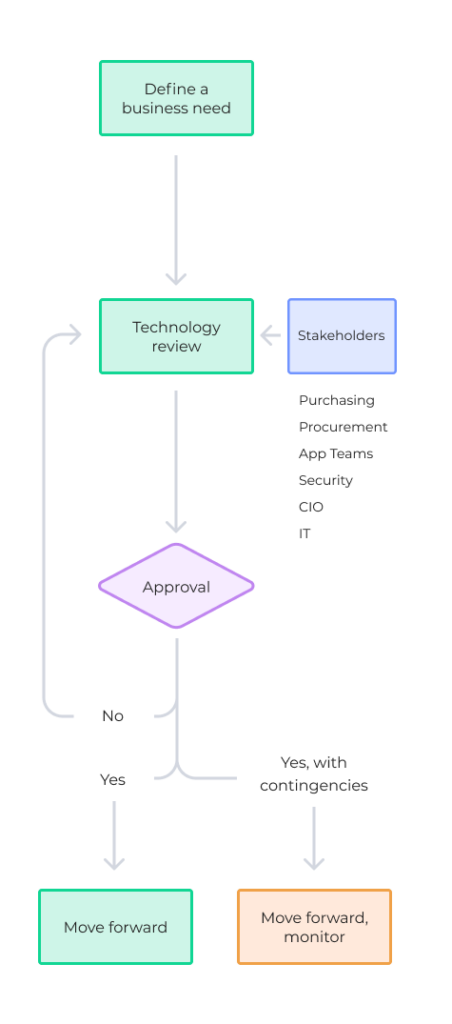
- Define a business need: The process starts with the business unit defining a need and then working with procurement once a product has been selected to help solve the problem.
- Schedule a technology review: Next, the Chief Information Officer (CIO), IT, application, and security teams review the product to determine if it meets the security and technical requirements of your organization.
- Get approval to proceed: If the product does not meet these requirements, it goes back to the business unit and procurement team, who must work with the supplier to meet the criteria or choose a different product. On the other hand, if the security requirements are met, it goes into the contracting phase and a deeper technology review. From there, the IT team reviews to determine whether they have the resources to implement the solution. Once approved, a project manager is assigned.
- Approval with contingencies: Sometimes, a product may be approved with contingencies. For example, a supplier may say, “We don’t support multi-factor authentication (MFA) now, but it’ll be ready in two to four weeks with the next version.” With that caveat in place, your security team may choose to move forward.
Schindler points out, “I’m not trying to harm the business or slow it down, but there’s no reason to move into a technology that we’re going to have to rip out because of regulatory requirements later on.”
Develop metrics and reassess regularly
Follow-up and continuous monitoring are as crucial as onboarding when it comes to new technology. The application may have been the perfect fit for your business needs at the time, but things change, and technology has to either evolve or get replaced as the requirements change.
You can get into an unstable situation even with technology suppliers that were once approved if you don’t consistently go back and re-check them. Establish metrics to measure performance levels and then reassess quarterly to ensure your business needs and security requirements are still met.
Manage suppliers post-implementation
Third-party access management is an essential part of procurement, especially when you’re dealing with suppliers who will have access to sensitive company information or systems. You’re handing your data off to another company and have to hold that third-party company to the same security standard you hold yourself to. Properly managing third-party access can help mitigate risks like data breaches, theft, and fraud.Having clear policies for granting, monitoring, and revoking third-party access is critical. These should include guidelines for managing passwords, access privileges, and data retention. That’s why it’s essential to have a workflow for removing access when you no longer work with a supplier. Graphite takes care of third-party risk assessments with automated reviews that help you more easily keep tabs on every supplier with whom you work.
Running Security in a Mature Procurement Environment
Schindler points out there are four things procurement must do (and do well) to ensure security is built into the entire process. You must:
- Align with the business: Understand your company’s mission, vision, and values and engage with your peers and executive leadership team to know what’s critical to business operations.
- Define your desired security state: Work with IT and security to establish the appropriate security and technology standards and ensure consistent supplier performance.
- Identify your metrics: Determine how you will measure the effectiveness of those controls regularly.
- Provide visibility to senior leadership: Prove the effectiveness of the product or technology to help executive teams make more informed strategic decisions for the company.
Prove ROI to Senior Leadership
You have to prove your value to company leaders. The CEO and board generally view security as insurance. Insurance that all of your data and credit card information is protected. Insurance that regulatory requirements are met.
When leadership questions the investment in your security program each year, it can be tempting to respond defensively. However, reframing the conversation can be a more effective approach. Emphasize that the organization was protected from potential security incidents because of the proactive measures taken. This highlights the value of investing in security measures and shows that the security program works as intended. Ultimately, by presenting a clear and compelling case for the security program’s value, you can help your organization prioritize and allocate resources more effectively.
Furthermore, benchmarking your security investment and process with peer organizations and companies is an excellent way to ensure that you are spending appropriately on security. By comparing your organization’s security practices and budget to those of similar organizations, you can gain valuable insights into whether you are spending too much, too little, or just the right amount on security. By learning from the security practices of other companies, you can also gain ideas and inspiration for improving your own security posture.
What’s next?
Graphite Connect is a proven comprehensive supplier lifecycle and risk management tool for procurement teams. We’ve taken it a step further, making it even easier for you to engage with security as an integral part of your procurement process—from onboarding new technology to implementation and beyond. Explore how Graphite can help you collaborate more effectively with security and IT to mitigate risk and drive business value.
Request a DemoReference:
¹ Jim Brennan, “Don’t Fear Shadow IT: Embrace IT,” Forbes, May 18, 2022.
www.forbes.com/sites/forbestechcouncil/2022/05/18/dont-fear-shadow-it-embrace-it/?sh=5e5d18971927